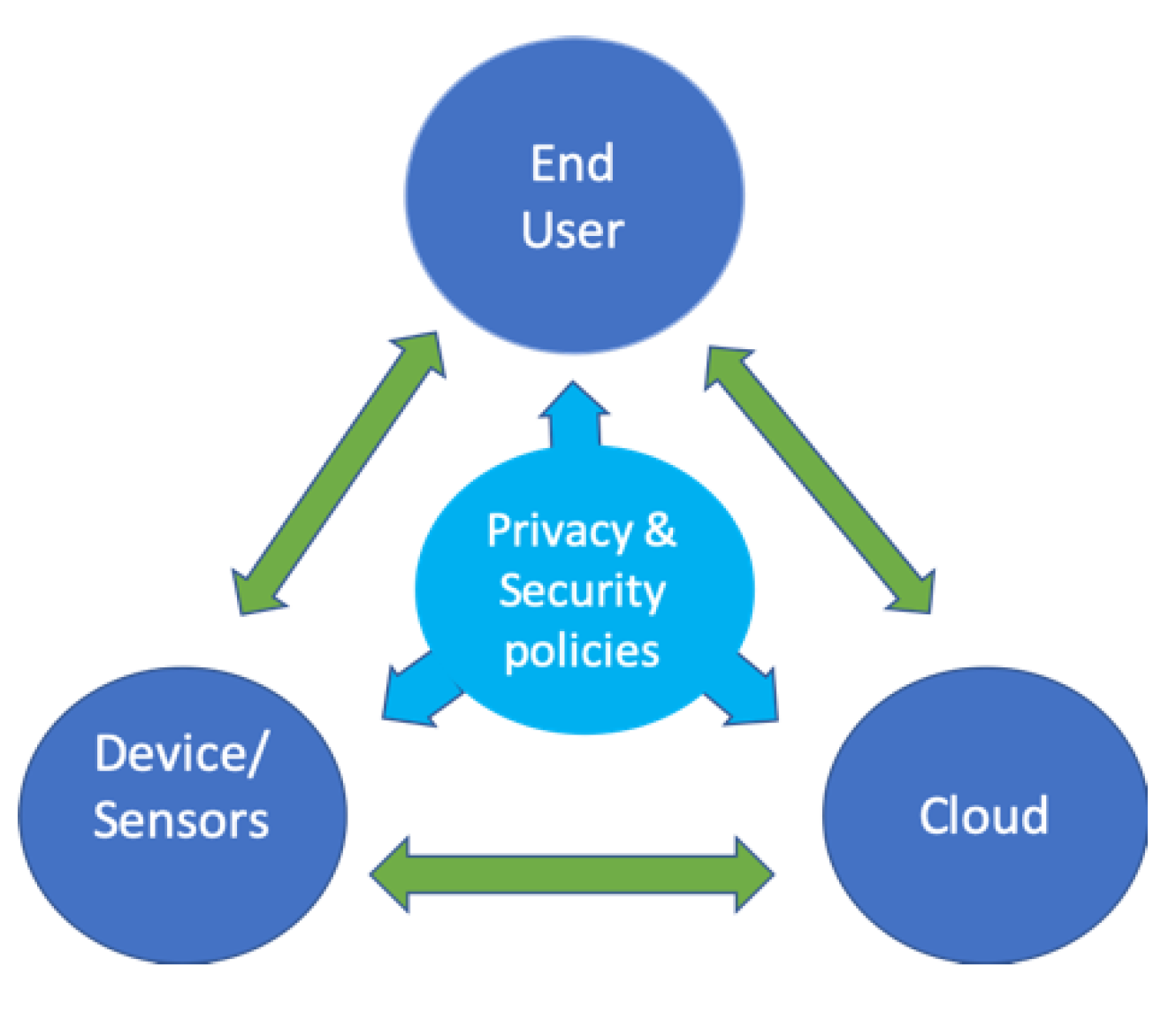
Privacy is a crucial aspect of our digital lives. It protects our personal information from misuse.
In the world of cybersecurity, privacy matters more than ever. With increasing online threats, safeguarding our data is vital. Privacy ensures our sensitive information stays safe from prying eyes. But what exactly is privacy in the digital age? Why is it so important?
And what challenges do we face in maintaining it? In this blog post, we will explore the significance of privacy in cybersecurity. We’ll also discuss the common challenges and practical solutions. Understanding these aspects can help you stay protected online. Let’s dive into the world of digital privacy and see how we can keep our data secure.
Credit: www.mdpi.com
Privacy In The Digital Age
Privacy has taken on new dimensions in the digital age. With the rise of the internet, social media, and smart devices, our personal data is more accessible than ever. Understanding privacy today means looking at how it has evolved and how technology impacts it.
Evolution Of Privacy
Privacy was simpler in the past. People kept personal information in physical forms, like diaries or photo albums. Only trusted friends and family had access to this information. With the advent of the internet, privacy began to change. Personal data started moving online. Emails replaced letters. Digital photos replaced printed ones.
In the early days of the internet, users were less aware of privacy issues. They shared personal details freely. Over time, awareness grew. People began to realize the risks of sharing too much online. Companies and governments also started recognizing the importance of protecting personal data.
Impact Of Technology
Technology has greatly impacted privacy. Smartphones, social media, and cloud storage have made it easier to share and store information. But they also make it easier for others to access that information. Social media platforms often collect user data to target ads. This can feel intrusive.
Another challenge comes from smart devices. Many homes have smart speakers, cameras, and other connected devices. These devices can collect data on users’ habits and preferences. Hackers can exploit these devices, leading to privacy breaches.
On the flip side, technology also offers solutions. Encryption can protect data from unauthorized access. Privacy settings on social media allow users to control who sees their information. Awareness and education about online privacy have improved.
Credit: appinventiv.com
Importance Of Privacy
The importance of privacy in cybersecurity cannot be overstated. Privacy is essential for protecting personal information from unauthorized access. It maintains the integrity and confidentiality of data. Without privacy, personal and sensitive information could be exposed to malicious entities. This could lead to various negative consequences. Let’s delve deeper into why privacy is crucial, focusing on personal security and trust in digital services.
Personal Security
Privacy is critical for personal security. By safeguarding personal data, individuals can protect themselves from identity theft. Hackers often target personal information to commit fraud. Protecting privacy helps prevent such incidents.
Also, privacy ensures that personal activities remain confidential. This includes online searches, communications, and transactions. Keeping this information private reduces the risk of cyber-attacks. It also protects against unwarranted surveillance.
Here are some key reasons why personal security is important:
- Protects against identity theft
- Prevents financial fraud
- Maintains confidentiality of personal activities
- Reduces risk of cyber-attacks
Trust In Digital Services
Privacy is essential for building trust in digital services. Users are more likely to engage with services that guarantee their data is safe. Trust is a key factor in the digital economy. Services that respect privacy gain more users.
When users trust a service, they are more likely to share personal information. This helps businesses provide better and more personalized services. On the other hand, breaches in privacy can severely damage trust. It can lead to loss of customers and revenue.
Consider the following points to understand the importance of trust:
- Encourages user engagement
- Enhances customer loyalty
- Supports personalized service offerings
- Prevents reputational damage
In summary, the importance of privacy in cybersecurity is clear. It is vital for personal security and building trust in digital services.
Cybersecurity Threats
Cybersecurity threats are growing. These threats put personal data at risk. They also affect businesses. Understanding these threats is vital. It helps in creating better security measures. This section will dive into common cyber threats and data breaches.
Common Cyber Threats
Cyber threats come in various forms. Here are some common types:
- Phishing: Fraudulent attempts to get sensitive information.
- Malware: Malicious software that damages or disrupts systems.
- Ransomware: Malware that encrypts files and demands payment for decryption.
- Denial-of-Service (DoS) Attacks: Overloading a network to make it unusable.
- Man-in-the-Middle (MitM) Attacks: Intercepting and altering communication between two parties.
Data Breaches
A data breach occurs when unauthorized access is gained to confidential data. This data might include personal information, financial details, or intellectual property. The impacts of data breaches are severe. They lead to financial loss and damage to reputation. Here are some key aspects of data breaches:
- Causes: Human error, weak passwords, and unpatched software.
- Consequences: Identity theft, financial loss, and legal penalties.
- Prevention: Strong passwords, regular updates, and employee training.
Implementing these measures can help in reducing the risk of data breaches.
Challenges In Maintaining Privacy
Maintaining privacy in the digital age is a complex task. Many challenges arise that make it difficult to protect personal data. This section explores some of the main obstacles that hinder privacy efforts. Understanding these challenges can help in developing better solutions.
Regulatory Hurdles
Different countries have varying privacy laws. Complying with all regulations is tough for global companies. Laws change frequently, adding to the complexity. Businesses need to stay updated to avoid penalties. This requires significant time and resources.
Technological Barriers
Technology evolves rapidly. New threats emerge constantly. Keeping up with these changes is challenging. Older systems may not support new security measures. Upgrading systems is expensive. Cybercriminals often use advanced tools. Staying ahead of them requires continuous investment in technology.
Strategies For Protecting Privacy
Protecting privacy in the digital age is crucial. Cyber threats continue to evolve, posing significant risks. Effective strategies can help safeguard personal and sensitive information. Below, we explore key strategies for protecting privacy.
Encryption Techniques
Encryption is a powerful tool in cybersecurity. It transforms readable data into unreadable code. Only authorized users with the decryption key can access the original information. This helps protect data from unauthorized access.
There are various types of encryption techniques. Symmetric encryption uses the same key for encryption and decryption. Asymmetric encryption uses a pair of keys: a public key and a private key. The public key encrypts the data, while the private key decrypts it. Both methods are essential for different use cases.
Advanced encryption standards (AES) are widely used. AES provides strong security and is efficient in performance. It is crucial for securing sensitive data in many applications.
Secure Communication
Secure communication ensures that data transmitted over networks remains confidential. One common method is the use of Secure Sockets Layer (SSL) and Transport Layer Security (TLS). These protocols encrypt data during transmission. They help protect information from interception and tampering.
Virtual Private Networks (VPNs) are another effective solution. A VPN creates a secure tunnel for data to travel through. This protects the data from being accessed by unauthorized users. VPNs are especially useful for remote workers and travelers.
End-to-end encryption (E2EE) is vital for secure messaging. E2EE encrypts messages on the sender’s device. Only the intended recipient can decrypt and read them. This ensures that even service providers cannot access the content of the messages.
Implementing these secure communication methods helps maintain privacy. They ensure that sensitive data remains protected during transmission.

Credit: fastercapital.com
Role Of Governments
Governments play a critical role in protecting privacy. They create laws and regulations to safeguard personal data. These rules help to ensure that organizations handle data responsibly. Governments also enforce compliance, ensuring that entities follow the rules.
Privacy Laws
Privacy laws are essential for protecting personal information. They set guidelines on how data should be collected, used, and shared. These laws also provide individuals with rights over their data. For example, the General Data Protection Regulation (GDPR) in the EU gives citizens control over their personal information. The California Consumer Privacy Act (CCPA) in the US offers similar protections.
Privacy laws often include:
- Data collection limitations
- Consent requirements
- Data breach notifications
- Rights to access and delete data
Regulations And Compliance
Regulations ensure that organizations follow privacy laws. Compliance means adhering to these rules. Governments monitor and enforce compliance through audits and fines. Non-compliance can lead to severe penalties and loss of trust.
Key compliance requirements often include:
- Appointing a Data Protection Officer (DPO)
- Conducting regular data protection impact assessments
- Implementing robust security measures
- Providing training to employees
Organizations must stay updated on changes in regulations. This helps them maintain compliance and protect user data.
Corporate Responsibility
Corporate Responsibility in cybersecurity is more crucial than ever. Companies must ensure the privacy of their users. This involves implementing strict data protection measures. Here, we discuss how organizations can uphold their responsibility through effective data handling policies and obtaining user consent.
Data Handling Policies
Companies need well-defined data handling policies. These policies dictate how data is collected, stored, and processed. A robust policy protects against data breaches and misuse.
Key elements of a strong data handling policy include:
- Data encryption
- Access controls
- Regular audits
Encryption ensures that even if data is intercepted, it remains unreadable. Access controls limit who can view or use the data. Regular audits help in identifying and fixing vulnerabilities.
User Consent
Obtaining user consent is vital. Users must know what data is collected and how it will be used. Transparency builds trust and ensures compliance with regulations.
Steps to effectively obtain user consent include:
- Clear communication
- Opt-in mechanisms
- Easy-to-understand terms
Clear communication means using simple language. Opt-in mechanisms ensure users actively agree to data collection. Easy-to-understand terms make sure users know their rights and choices.
By focusing on these aspects, companies can better protect user privacy and enhance their cybersecurity posture.
Future Of Privacy
The future of privacy in cybersecurity holds many challenges and opportunities. As technology advances, protecting personal data becomes more complex. Understanding emerging technologies and global trends is essential to stay ahead.
Emerging Technologies
New technologies like AI and IoT are changing privacy norms. AI can analyze vast amounts of data quickly. This raises concerns about data misuse. IoT devices collect personal information constantly. They create new vulnerabilities. Blockchain offers some solutions. It provides a secure way to store data. But it is not yet widely adopted.
Quantum computing is another emerging technology. It has the potential to break current encryption methods. This could make existing security measures obsolete. Preparing for these changes is crucial. Developing new encryption methods will be necessary.
Global Trends
Global privacy laws are evolving. Regulations like GDPR and CCPA set new standards. Companies must comply with these laws. Failure to do so can result in hefty fines. Different countries have different regulations. This creates complexity for global businesses.
Consumer awareness is also rising. People are more concerned about their privacy. They demand better protection from companies. This shift influences how businesses handle data. Transparency and trust have become key factors.
Cyberattacks are becoming more sophisticated. Attackers use advanced techniques to breach security. Staying updated with the latest threats is essential. Continuous monitoring and updating security measures help mitigate risks.
The future of privacy in cybersecurity requires vigilance. Embracing new technologies and understanding global trends will be crucial. Ensuring privacy while leveraging technology remains a delicate balance.
Frequently Asked Questions
What Is Privacy In Cybersecurity?
Privacy in cybersecurity means protecting personal data from unauthorized access. It ensures that information stays confidential and secure.
Why Is Privacy Important In Cybersecurity?
Privacy is important because it protects sensitive data. It helps prevent identity theft, fraud, and data breaches.
What Are The Main Privacy Challenges In Cybersecurity?
Main privacy challenges include data breaches, phishing attacks, and malware. They threaten the security of personal information.
How Can Individuals Protect Their Privacy Online?
Individuals can use strong passwords, update software regularly, and avoid sharing personal information on unsecured websites.
What Solutions Exist For Enhancing Privacy In Cybersecurity?
Solutions include encryption, multi-factor authentication, and secure networks. These methods help protect data and ensure privacy.
Conclusion
Privacy is crucial in today’s digital world. It protects our personal information. Cybersecurity faces constant challenges. Hackers grow smarter every day. Effective solutions are essential. Strong passwords, encryption, and awareness can help. Everyone must play a part. Stay informed and vigilant.
Your data is valuable. Protect it wisely. By understanding the importance of privacy, you can take action. Make cybersecurity a priority. Stay safe online.